Enforce Sharing Rules When Apex Launches a Flow
December 25, 2024When Apex launches a flow, ensuring data visibility and access control becomes paramount. Enforcing sharing rules is crucial for maintaining data integrity and preventing unauthorized access. This article delves into the nuances of sharing rules in the context of Apex-launched flows, providing practical solutions and best practices to ensure your data remains secure and accessible only to the right users.
Understanding Sharing Rules in Apex-launched Flows
Sharing rules are a powerful mechanism in Salesforce for extending access to records beyond the standard organization-wide defaults. However, when Apex initiates a flow, the context under which the flow operates can sometimes bypass these crucial sharing rules, leading to potential data breaches or inconsistencies. Understanding how sharing rules interact with Apex is the first step towards implementing effective data security measures.
How to Enforce Sharing Rules When Apex Launches a Flow
There are a few key strategies to ensure sharing rules are enforced when your Apex code kicks off a flow.
-
with sharingKeyword: The simplest and often most effective method is using thewith sharingkeyword in your Apex class. This keyword ensures the flow runs in the context of the current user, inheriting their sharing rules. This means the flow can only access records the user has permission to see. -
without sharingKeyword (with caution): While thewithout sharingkeyword can be useful in specific scenarios, it should be used with extreme caution when dealing with flows that handle sensitive data. Using this keyword bypasses sharing rules altogether, allowing the flow to access all records, regardless of the user’s permissions. If you must usewithout sharing, implement stringent security checks within the flow itself to restrict access to sensitive information. -
Apex Sharing Recalculation: In some complex scenarios, sharing calculations might need to be refreshed manually after records are created or modified within the flow. Apex provides methods for recalculating sharing rules, ensuring data visibility is accurate and reflects the latest changes.
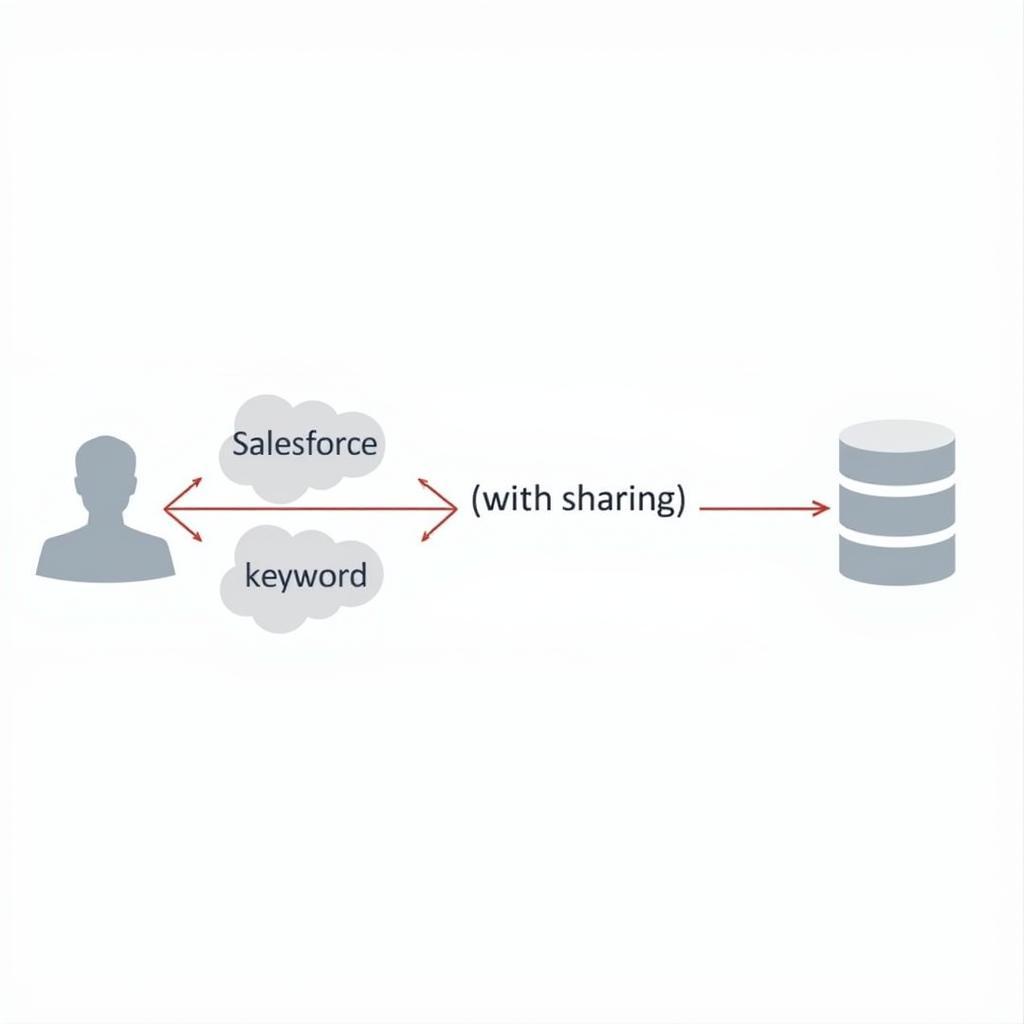 Enforcing Sharing Rules in Apex-launched Flows
Enforcing Sharing Rules in Apex-launched Flows
Best Practices for Sharing Rule Enforcement
To maximize security and ensure consistent application of sharing rules, consider these best practices:
-
Minimize
without sharingUsage: Strive to avoid usingwithout sharingwhenever possible, especially when working with sensitive data. If it’s absolutely necessary, ensure your flow has robust internal security mechanisms. -
Regularly Review Sharing Rules: Conduct periodic audits of your sharing rules to ensure they are up-to-date and aligned with your organization’s security policies.
-
Test Thoroughly: Test your Apex code and flows extensively to validate that sharing rules are being correctly enforced under various scenarios. This includes testing with users having different profiles and roles.
Common Scenarios and Troubleshooting
Here are a few common scenarios developers encounter when dealing with sharing rules and Apex-launched flows:
-
Scenario 1: Records created within a flow launched by Apex with
without sharingare not visible to the user. Solution: Recalculate sharing rules using Apex after record creation. -
Scenario 2: A flow launched with
with sharingis unable to access related records. Solution: Ensure the user has access to the related records via sharing rules or role hierarchy.
Securing Your Data: A Holistic Approach
Enforcing sharing rules is just one piece of the puzzle when it comes to securing your Salesforce data. A comprehensive security strategy should include a combination of measures, such as profile and permission set configurations, field-level security, and regular security audits.
Conclusion
Enforcing sharing rules when Apex launches a flow is essential for maintaining data integrity and preventing unauthorized access. By understanding the nuances of sharing rules and applying the best practices outlined in this article, you can effectively protect your Salesforce data while ensuring authorized users have the necessary access to perform their tasks. By using the with sharing keyword diligently and minimizing the use of without sharing, you can strike the right balance between security and functionality.
FAQ
- What is the
with sharingkeyword in Apex? - How can I recalculate sharing rules using Apex?
- What are the risks of using the
without sharingkeyword? - How can I test my sharing rules effectively?
- What are the other security measures I should consider in Salesforce?
- How do sharing rules interact with role hierarchy?
- What are the best practices for managing sharing rules in a complex organization?
 FAQ about Sharing Rules in Apex
FAQ about Sharing Rules in Apex
Need More Help?
For further assistance with enforcing sharing rules or any other Salesforce-related inquiries, contact us at Phone Number: 0915117113, Email: [email protected] or visit us at Address: To 3 Kp Binh An, Phu Thuong, Viet Nam, Binh Phuoc 830000, Viet Nam. Our customer support team is available 24/7.